In 2025, internet filter will remain a pervasive issue affecting millions of users worldwide. Internet filter is a growing concern as more countries implement stringent measures to control online content. According to the latest report from Freedom House, global internet freedom has declined for the 13th consecutive year. So it’s crucial to understand the current landscape of internet censorship, which countries are most affected, how content is filtered, and most importantly, how to bypass and unblock restrictions with feasible tools through this article.
Which Countries Have Significant Internet Filters in 2025?
It’s widely acknowledged that the five countries including Bahrain, China, Iran, Syria, and Vietnam are listed as State Enemies of the Internet in 2013 due to their strict internet censorship policy.

But as of 2024, several countries stand out for their extensive internet filter practices:
- China‘s “Great Firewall” is one of the most well-known internet censorship systems. It blocks access to major platforms like Google, Facebook, and Twitter, while heavily monitoring domestic sites. The government employs a combination of technological and human resources to enforce its stringent online content policies.
- Iran employs a sophisticated filtering system to control what its citizens can access online. The government targets political content, social media, and platforms that challenge its narrative. Following political unrest, Iran has intensified its efforts, using both technological and regulatory means to suppress dissent.
- Russia has increased its internet censorship efforts, requiring data to be stored on local servers and blocking sites that do not comply with its regulations. The government has expanded its control over internet infrastructure, allowing it to monitor and restrict access to content deemed threatening to national security.
- Saudi Arabia filters a wide range of content, including political, religious, and social material that it deems inappropriate. The government uses a combination of IP blocking, DNS filtering, and keyword filtering to enforce its internet censorship policies.
What Content is Usually Filtered?
Many countries around the world implement internet filters to various degrees. The types of content filtered can vary based on the political, social, and cultural goals of the governments in these countries. The primary categories of filtered content include:

- Political Content:
- Websites and articles critical of the Iranian government.
- Content promoting political dissent or opposition groups.
- Foreign news outlets reporting on Iran’s political situation.
- Social Media Platforms:
- Major social media sites like Facebook, Twitter, and Instagram.
- Messaging apps such as Telegram and WhatsApp.
- Platforms used for organizing protests or sharing dissenting views.
- News Websites:
- Independent and international news sources.
- Sites reporting on human rights abuses in Iran.
- Websites covering sensitive topics like corruption within the government.
- Religious Content:
- Material contradicting the state-approved version of Islam.
- Content related to other religions or sects deemed heretical.
- Websites promoting secular or atheistic views.
- Adult Content:
- Pornographic websites.
- Sex education sites are not aligned with the state’s moral standards.
- Entertainment and Lifestyle:
- Movies, music, and books that challenge conservative values.
- LGBTQ+ content.
- Sites promoting Western lifestyles or cultures.
- Educational Resources:
- Academic articles and books that discuss topics sensitive to the regime.
- Online courses and materials from foreign institutions that promote critical thinking or liberal arts education.
- Privacy and Security Tools:
- VPN services and proxy sites.
- Encryption tools and privacy-focused software.
- Websites offering advice on circumventing censorship.
Related article: How to Unblock a Website on iPhone? (5 Feasible Ways)
Common Methods for Internet Filter
Internet filters, often employed by governments, organizations, and educational institutions, involves various techniques to control access to certain types of content on the web. These methods ensure that only approved content is accessible while blocking potentially harmful or inappropriate material.
Here are some common methods for internet filters.
1. Keyword-Based Filtering
Keyword-based filters scan the content of websites for specific keywords or phrases that are on a blocklist. If any of these keywords are detected, access to the site is denied. Keywords might include flagged terms related to pornography, violence, hate speech, or politically sensitive topics. When these keywords are found, the website is blocked.
Pros: Simple to implement and effective at catching specific terms quickly.
Cons: High probability of false positives, as legitimate content might use blocked keywords in a non-malicious context.
2. URL Blocking
This method involves maintaining a list of URLs that are blocked. When a user tries to access a website on this list, the connection is severed. Moreover, URL blocking can be applied to both HTTP and HTTPS traffic, ensuring that attempts to access blocked sites over secure connections are also intercepted.
Pros: Effective for blocking known harmful websites and adult content, especially those required to disclose their identifiers.
Cons: Requires regular updates and maintenance as new websites emerge and existing ones change URLs.
3. Content-Based Filtering
Instead of blocking specific URLs, content-based filtering blocks entire categories of websites, such as social media, gambling, or sites tagged with violence. As websites are tagged based on their content, so any site falling under a restricted category is blocked.
Pros: Provides a broader approach to filtering, which can be less labor-intensive than maintaining URL blocklists.
Cons: May inadvertently block useful websites that fall under a broad category (e.g., a social media site used for professional networking).
4. DNS Filtering
DNS filtering is a domain-level blocking that blocks entire domains rather than specific URLs. It scans the DNS requests that users make to access websites and blocks those linked to restricted domains. This method involves checking the IP addresses associated with domains and blocking access to those listed on the blocklist.
Pros: Useful for proactive security policies, minimizing the risk of malware and other network threats by blocking access to malicious domains.
Cons: Less granular than URL blocking, as it applies blanket restrictions to all content under a domain, potentially blocking access to useful subpages.
How Web Filters Operate?
1. User Request: A user attempts to access a website.
2. Content Scanning: The web filter scans the requested page, domain, or website against its index of allowed content.
3. Access Decision:
- No Violations Found: If the content passes the filter’s criteria, access is granted.
- Violation Detected: If the content triggers a flag, the website is blocked and the connection is severed.
7 Solutions to Bypass Internet Filters
This part will walk you through 7 most effective strategies to bypass internet filters, giving you the tools to access the content you need.
1. Virtual Private Networks (VPNs)
For those seeking to bypass these restrictions, BearVPN offers a reliable solution. It provides a reliable solution for bypassing internet filtering, ensuring unrestricted access to the web by:
- Traffic Encryption: BearVPN uses AEs-256 technology to encrypt your internet traffic, making it unreadable to your ISP and government authorities. This ensures your online activities remain private and secure from monitoring and censorship.
- IP Address Masking: By connecting to BearVPN, your real IP address is replaced with one from the VPN server, making it appear as though you are browsing from a different location. This helps you bypass local restrictions and access blocked content.
- Bypassing Geo-Restrictions: With a wide 5000+ network of servers in 120+ countries, BearVPN allows you to connect to servers outside your country. This enables you to access websites and services that are restricted in your region.
- Avoiding Throttling: BearVPN hides your online activities from your ISP, preventing them from throttling your connection based on your usage. This results in a faster and more consistent internet experience.
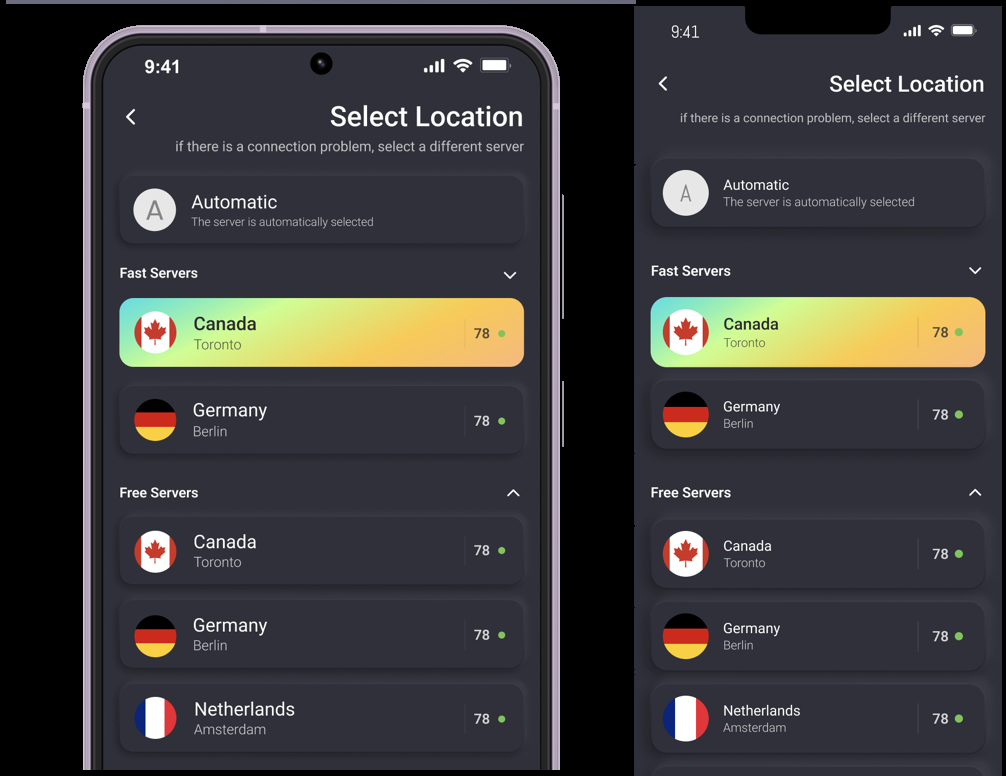
How to Use BearVPN as Filtering Breaker?
- Download and install BearVPN app from the official website or your device’s app store.
- Select a free server location in a country with fewer restrictions.
- Tap the connect button to unlock restrictions. Once connected, you can access previously restricted content.
2. Proxy Servers
Proxy servers act as intermediaries, fetching web content on your behalf. They’re useful for basic filtering but have limitations.
A proxy server sits between your device and the internet. When you request a website, your request first goes to the proxy. The proxy then fetches the content from the website and sends it back to you. This process hides your direct IP address from the destination website.
It can bypass basic IP-based or URL-based filters. Less effective against more sophisticated content filters or deep packet inspection (DPI).
Web proxies are easy to use but are often slow and less secure. Dedicated proxy services (SOCKS5, HTTP/S) offer more flexibility and better performance but require manual configuration.
- Choose your proxy type like web proxy or dedicated Proxy (SOCKS5, HTTP/S) service provider.
- Configure Your Access:
- For Web Proxies: Simply type the URL of the website you want to visit into the provided input field on the web proxy site and click “Go” or “Browse.”
- For Dedicated Proxies:
- Browser Settings: Go to your browser’s settings (e.g., Chrome: Settings > System > Open your computer’s proxy settings; Firefox: Settings > Network Settings > Manual proxy configuration).
- Enter Proxy Details: Input the IP address and port number for the HTTP, HTTPS, and/or SOCKS proxy as provided by your service.
- Save your changes.
3. Tor Browser
Tor (The Onion Router) is a powerful tool for anonymity and bypassing censorship by routing your traffic through a decentralized network.
Tor routes your internet traffic through a decentralized network of volunteer-operated servers worldwide. Each relay decrypts one layer of encryption, revealing the next relay’s address, until the traffic exits to the internet. This multi-layered routing provides strong anonymity and bypasses many filters.
However, it can be significantly slower than direct connections or VPNs due to the multi-hop routing. Tor traffic can sometimes be blocked by advanced filters, but “Tor bridges” (unlisted relays) can help bypass this.
- Download Tor Browser: Visit the official Tor Project website and download the Tor Browser bundle for your operating system.
- Install and Launch: Run the installer. Once installed, launch the Tor Browser application. It will automatically attempt to connect to the Tor network.
- Connect to Tor Network: Click “Connect” when prompted. If you’re in a heavily censored region, you might need to configure “bridges” in the Tor Browser settings to establish a connection.
- Begin Browsing: Once connected, a new browser window will open. All traffic through this browser is now routed through the Tor network, providing enhanced anonymity and filter bypass capabilities.
4. DNS over HTTPS (DoH) or DNS over TLS (DoT): Encrypting Your Lookups
These protocols encrypt your DNS queries, preventing your Internet Service Provider (ISP) or network administrator from seeing which websites you’re trying to visit based on DNS lookups.
When you type a website address (like “example.com”) into your browser, your computer performs a DNS (Domain Name System) query to find the website’s IP address. DoH and DoT encrypt these queries, preventing your ISP or network from intercepting and blocking them.
It’s effective against DNS-based filtering, where specific domains are blocked by resolving them to a non-existent or blocked IP address.
While they hide your DNS requests, they don’t hide the actual connection to the website, so other filtering methods (like IP blocking) can still apply.
- Choose a DoH/DoT Provider: Popular public providers include Cloudflare (1.1.1.1), Google Public DNS (8.8.8.8), and Quad9 (9.9.9.9).
- Configure Your Browser (Easiest Method):
- Firefox: Go to Settings > General > Network Settings > Enable DNS over HTTPS. Select a provider or enter a custom one.
- Chrome: Go to Settings > Privacy and security > Security > Use secure DNS. Choose a provider or enter a custom one.
- Microsoft Edge: Go to Settings > Privacy, search, and services > Security > Use secure DNS. Choose a provider or enter a custom one.
- Configure Your Operating System (More Advanced): For system-wide DoH/DoT, you’ll need to adjust network settings in Windows, macOS, or Linux. This process varies by OS version; search for “configure DoH [your OS]” for specific instructions.
5. SSH Tunnels
If you have access to an SSH server outside the filtered network, you can create a secure tunnel to forward your internet traffic.
If you have access to an SSH server outside the filtered network, you can create an SSH tunnel to forward your internet traffic through it. This encrypts your traffic and makes it appear to originate from the SSH server, effectively bypassing local filters.
Highly effective for bypassing many filters, especially in corporate or educational environments.
But the point is it requires an SSH server (e.g., a rented VPS or a personal server) and technical knowledge to set up.
- Acquire an SSH Server: You’ll need credentials (IP address, username, password/key) for an SSH server located outside the filtered network.
- Use an SSH Client:
- Windows: Download and use a client like PuTTY.
- macOS/Linux: Use the built-in
sshcommand in your terminal.
- Create the Tunnel:
- PuTTY (Windows): Open PuTTY, enter your SSH server’s IP. Go to Connection > SSH > Tunnels. In the “Source port” field, enter a local port number (e.g., 8080). Select “Dynamic” and click “Add.” Go back to Session and click “Open” to connect.
- Terminal (macOS/Linux): Open Terminal and type:
ssh -D 8080 user@your_ssh_server_ip(replace8080with your chosen local port,userwith your SSH username, andyour_ssh_server_ipwith the server’s IP).
- Configure Your Browser: Set your browser’s proxy settings to use a SOCKS5 proxy at
127.0.0.1(localhost) and the local port you chose (e.g.,8080).
6. Using Different Ports/Protocols
Some filters block traffic on specific ports. By using common ports for your bypass tools, you might slip through.
Some filters block traffic on specific ports (e.g., common VPN ports). Trying to use common ports like 443 (HTTPS) or 80 (HTTP) for VPNs or proxies can sometimes bypass filters that only inspect less common ports.
This method can work against less sophisticated firewalls, but it requires your VPN or proxy service to support these alternative ports or protocols.
- Check Your VPN/Proxy Settings: Open your VPN or proxy client’s settings.
- Look for Port Options: Search for options related to “connection type,” “protocol,” or “port.” You might see choices like “TCP 443,” “Stealth Mode,” “Obfuscated Servers,” or “Scramble.”
- Select an Alternative: Choose an option that uses a common web port (like 443 for HTTPS) or an obfuscation feature designed to mimic regular web traffic.
- Reconnect: Apply the changes and try to connect again.
7. Web-based Translators/Caches
This method is very basic and has significant limitations but can sometimes offer a glimpse of blocked content.
Services like Google Translate or Google Cache can sometimes be used to view content from blocked websites. This works because the request for the blocked content originates from Google’s servers, which are usually not blocked.
Nevertheless, it’s very limited. Only works for static web pages and often breaks site functionality (images, videos, interactive elements might not load). So it’s not a general-purpose bypass method. It’s a last resort for viewing text-based content.
- Go to the Service:
- Google Translate: Visit translate.google.com.
- Google Cache: In Google Search, search for the website you want. If the site appears in results, click the three dots next to the URL and select “Cached.”
- Enter the URL:
- Google Translate: In the translation box, type or paste the URL of the blocked website. Select a language to translate from (e.g., “Detect language”) and a language to translate to (e.g., “English”). Click the translated URL that appears in the output box.
- Google Cache: If available, the cached version of the page will load.
Conclusion
Internet Filter in 2024 continues to be a significant challenge in many parts of the world. Countries like China, Iran, Russia, and Saudi Arabia implement rigorous censorship measures to control online content. However, with tools like BearVPN, users can bypass these restrictions and enjoy unrestricted access to the internet.
Understanding the mechanisms behind Internet Filter and knowing how to circumvent them is crucial for maintaining internet freedom. BearVPN provides a practical and reliable solution for overcoming these challenges, ensuring that users can browse the web securely and freely.
Stay informed, stay secure, and keep exploring the digital world without boundaries.



